BitFire
enterprise class security for everyone
BitFire Install Guide »
Report Bug
·
Request Feature
Table of Contents
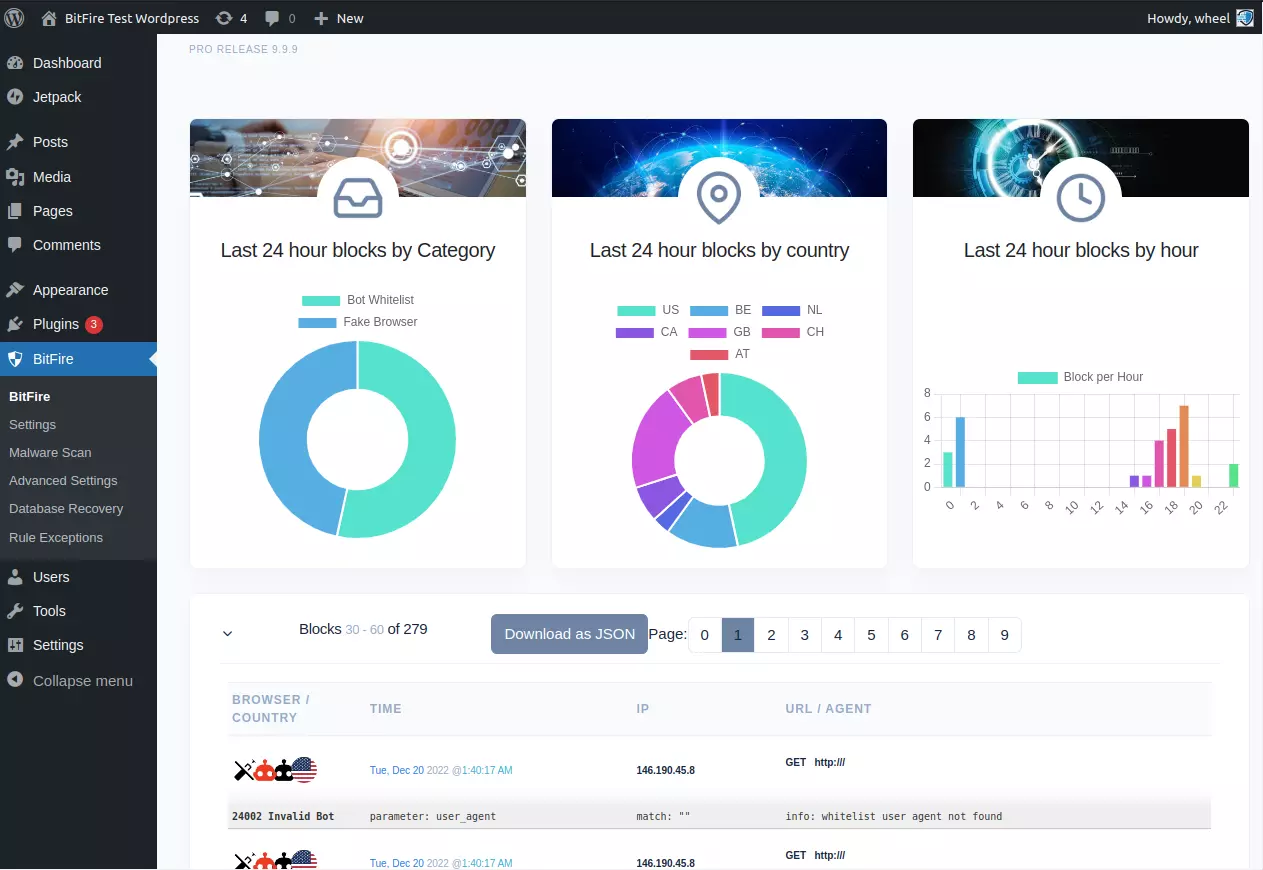
About BitFire
There are many choices for PHP firewalls to protect your webservers, most can be easily bypassed.
Here's How BitFire is different:
-
Speed. <2 ms block times - BitFire is up to 100x faster than the most popular PHP Firewalls
-
Bot authentication. Authenticates good bots like google, facebook, bing, ahrefs, by source network
-
Browser verification. Transparant JavaScript browser verification ensures user's are real
-
Client Integrity. Automatically generate browser policy preventing browser takeover
-
Server Integrity. Authenticated file access prevents server code modification
-
Grammer based firewall. Parses SQL, HTTP, HTML for the most accurate blocking
Built With
BitFire is built from pure PHP and has no external dependencies. BitFire can take advantage of several PHP shared memory caches including APCu, SHM, shmop and OpCache
Getting Started
Security from F to A in 5 minutes https://www.youtube.com/watch?v=DHhEW2otdng Install Guide: https://bitfire.co/bitfire-install
Prerequisites
You will need: a webserver (apache, nginx), PHP >= 7.1, a login, and a text editor.
Installation
-
Install via GitHub
git clone https://github.com/bitslip6/bitfire.git add: auto_prepend_file = "/path/to/bitfire/startup.php" to root .user.ini file - or Install via Composer
composer require bitslip6/bitfire add: auto_prepend_file = "/path/to/bitfire/startup.php" to root .user.ini file -
Bitfire is now installed! The default config will not block anything until enabled. set bitfire_enabled in
bitfire/config.iniand see the quickstart in this readme.bitfire_enabled = true;
- Congratulations! Time for a beer
Detailed configuration and installation is available on our Support Center
Setup / Configuration Quickstart
The default configuration is very conservative and will only block
bots identifying themselves as malicious scripts. The configuration is stored in config.ini in the BitFire
home directory (your github checkout location, or for composer vendor/bitslip6/bitfire/config.ini)
You can configure blocking by setting the dashboard_path and password ini configuration in config.ini. This file is made write only on first page view so you may need to update permission to allow read and write.
dashboard = "/bitfire_dashboard"; password = "aStrongSecurePassword";
Now visit your website at path "your_domain.com/bitfire_dashboard" enter the password when prompted, then click on "Settings" and configure the settings you want to use
On first page view BitFire will auto configure itself for your server and rarely needs to be adjusted.
Feature flags support 3 values:
- false: disable the feature
- report: don't block the traffic but add an entry to the report_file (config.ini setting)
- block: block the request, server response_code (config.ini) from views/block.php we recommend beginning with report and then moving to block only after verifying that you would not be blocking good traffic. https://github.com/bitslip6/bitfire/wiki/block_reporting for details.
1. Require full browser. If your website uses JavaScript and cookies (99% of all websites) you can require all web browers to prove they support both by enabling require_full_browser. Since >95% of all exploit scripts and worms do not support JavaScript or cookies this is the single best protection you can install to prevent breakins. This cookie is non user-identifying and so is fully GDPR compliant and does not require a GDPR notification.
require_full_browser = report | block2. Enable bot whitelist. Futher limit bots by allowing only verified whitelisted robots. A preconfigured list of common bots included with BitFire. Refer to our wiki for how to add additional bots.
whitelist_enable = report | block3. Enable core web filters. The web filter blocks malicious requets like XSS, LFI, RCE and SQLi as well as many others. The entire web filter can be enabled or disabled with the web_filter_enabled parameter. We recommend the following configuration:
web_filter_enabled = report | block
xss_block = report | block
web_block = report | block
file_block = report | block
sql_block = report | block4. Enable IP blocking. By default BitFire will not black list IP addresses. We recommend you enable this feature which allows for the fastest possbile drop of HTTP floods.
allow_ip_block = trueFor detailed documentation, please refer to the Documentation
Roadmap
See the open issues for a list of proposed features (and known issues).
Contributing
Additions to the bot whitelist and additional attack signatures or bypasses are greatly appreciated. If your contributions are included you will recieve discounts on comercial licencing for BitFire Pro.
- Fork the Project
- Create your Feature Branch (
git checkout -b feature/AmazingFeature) - Commit your Changes (
git commit -m 'Add some AmazingFeature') - Push to the Branch (
git push origin feature/AmazingFeature) - Open a Pull Request
License
Distributed under the Apache 2.0 License. See LICENSE for more information.
Contact
Cory - @bitslip6 - info@bitslip6.com
Project Link: https://github.com/bitslip6/bitfire