OWASP Security Knowledge Framework
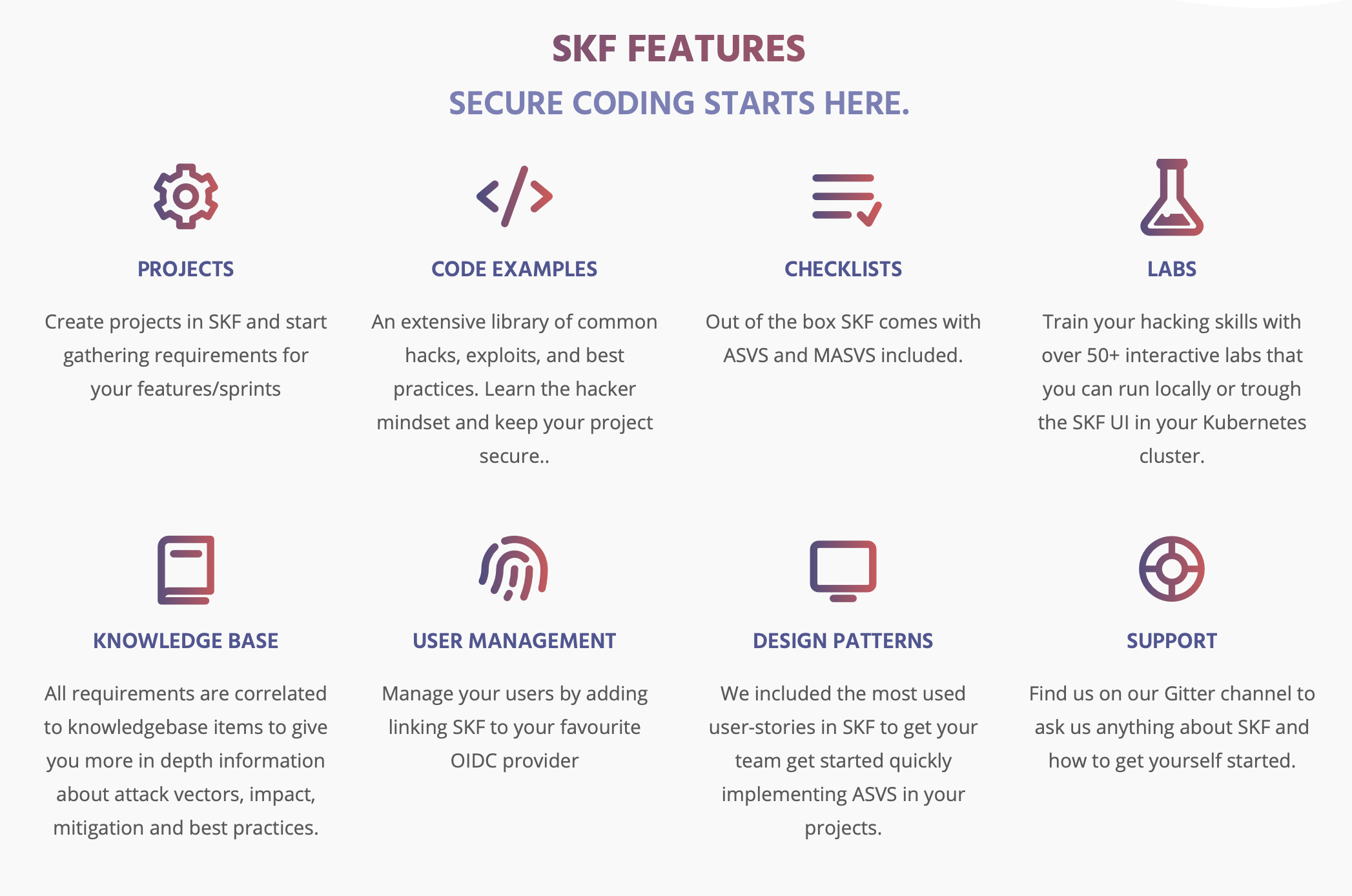
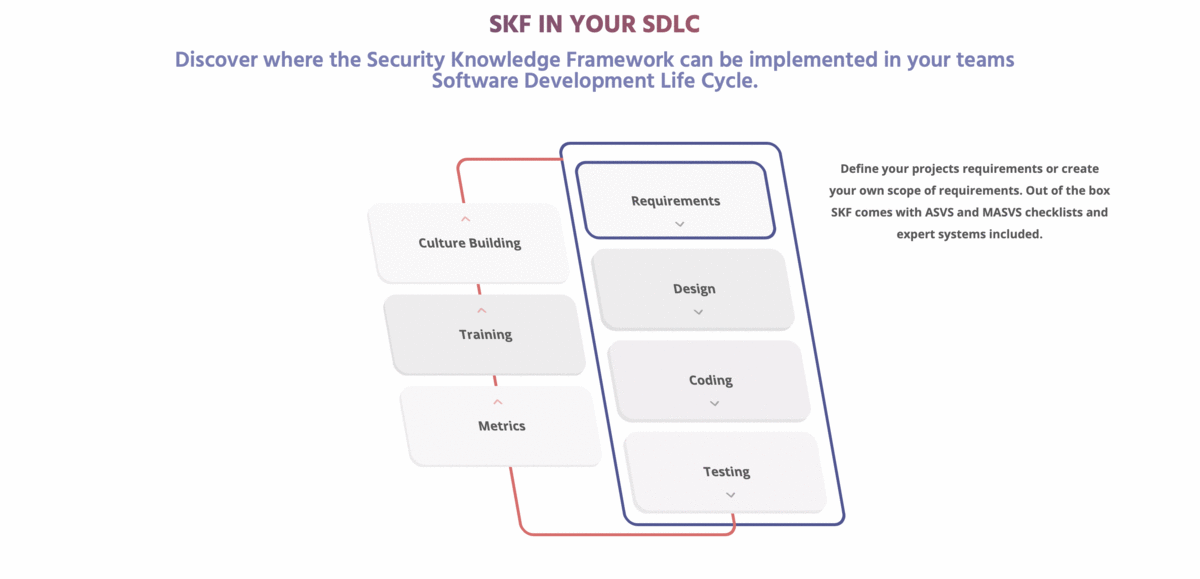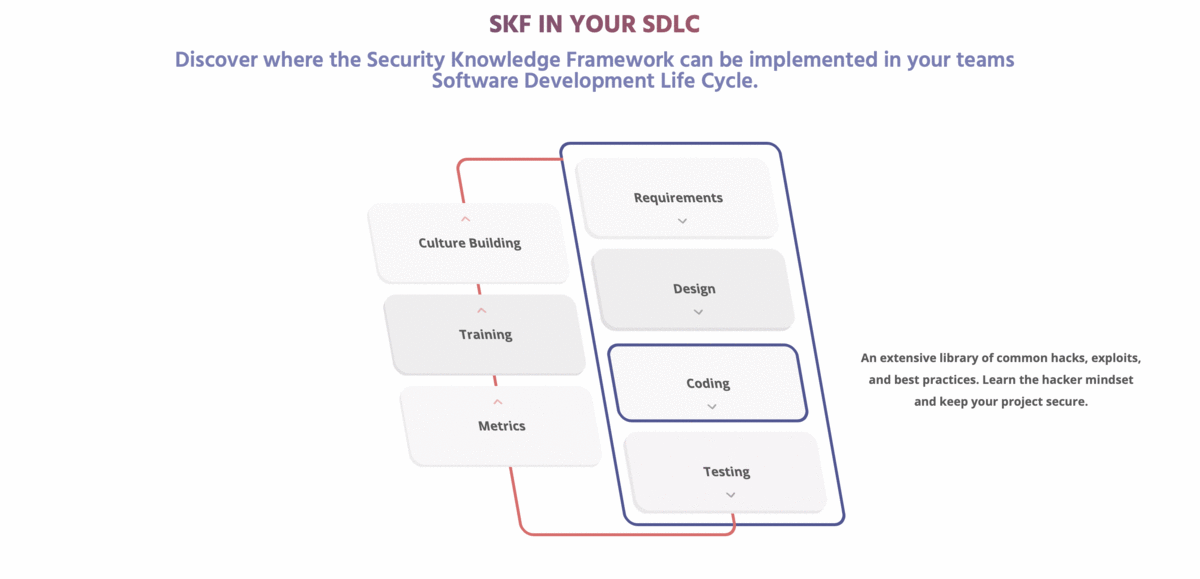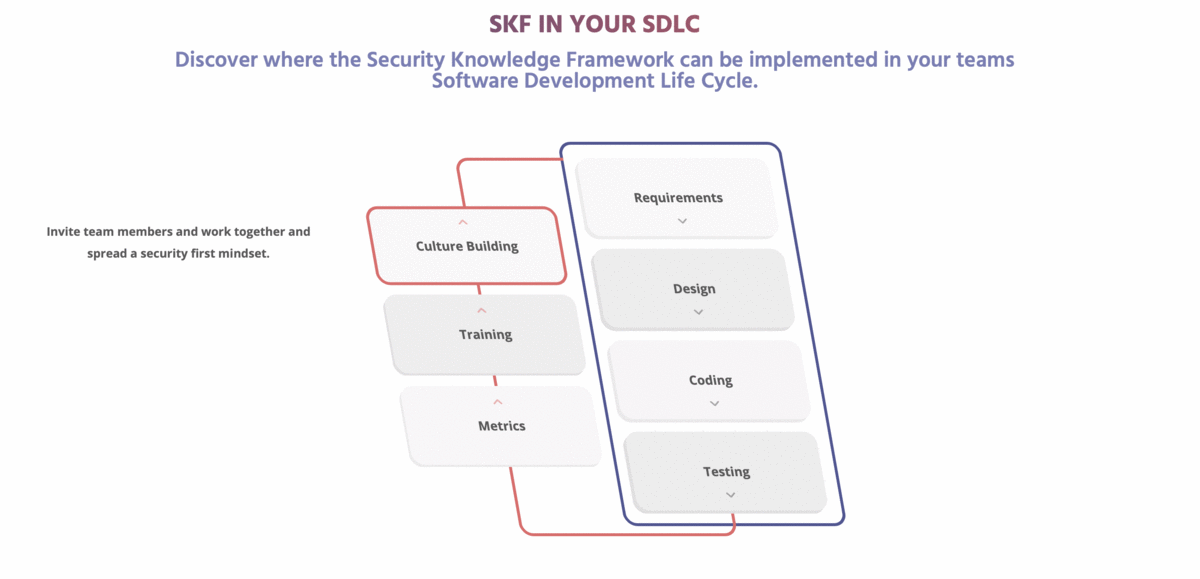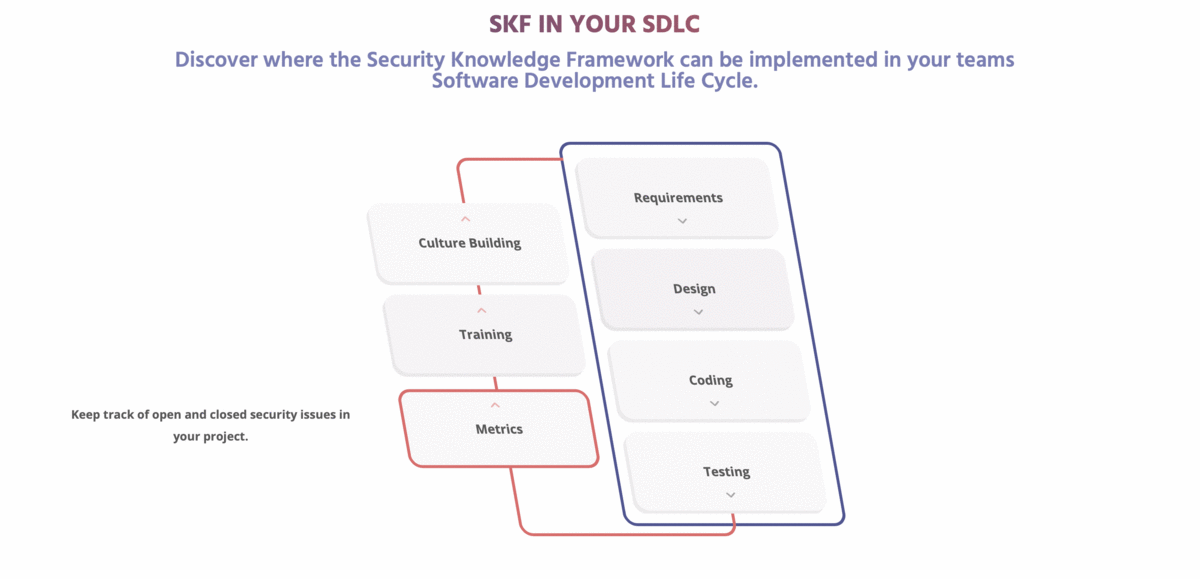
The OWASP Security Knowledge Framework is an open source web application that explains secure coding principles in multiple programming languages. The goal of OWASP-SKF is to help you learn and integrate security by design in your software development and build applications that are secure by design. OWASP-SKF does this through manageable software development projects with checklists (using OWASP-ASVS/OWASP-MASVS or custom security checklists) and labs to practice security verification (using SKF-Labs, OWASP Juice-shop, and best practice code examples from SKF and the OWASP-Cheatsheets).
Table of Contents
- Introduction
- Installing
- Updating Database
- Updating Chatbot
- Usage
- CI-Pipeline
- Development / Contributing
- Scrum Board
- License
- Contributors
Introduction
Our experience taught us that the current level of security of web-applications is not sufficient enough to ensure security. This is mainly because web-developers simply aren't aware of the risks and dangers that are lurking, waiting to be exploited by hackers.
Because of this we decided to develop a framework in order to create a guide-system available for all developers so they can develop applications secure by design from the start.
Installing
Kubernetes installation how to
Bare metal / on premise installation how to
Docker-compose local how to
SKF K8s Raspberry pi cluster how to
SKF Chatbot installation how to
Updating Database
There is a method available to update the content of the SKF application.
When you have modified or created new Knowledge base items, code examples or checklist you need to run the following commands in the SKF root directory:
export FLASK_APP=skf/app.py
export PYTHONPATH=.:$PYTHONPATH
flask updatedb
Updating chatbot
There is a method available to update the dataset of the SKF chatbot application.
When you have modified or created new Knowledge base items, code examples or checklist you need to run the following commands in the SKF root directory:
export FLASK_APP=skf/app.py
export PYTHONPATH=.:$PYTHONPATH
flask initdataset
Usage
For more detailed information such as setting up an admin account and user guides please see the extended documentation that can be found below:
Readme: extended documentation
CI-Pipeline
Travis-ci.org:
Test and Deploy with Confidence. Easily sync your GitHub projects with Travis CI and you'll be testing your code in minutes!
SKF Build details:
https://travis-ci.org/blabla1337/skf-flask
Coveralls.io Python:
DELIVER BETTER CODE. We help developers deliver code confidently by showing which parts of your code aren't covered by your test suite.
SKF Coveralls details:
https://coveralls.io/r/blabla1337/skf-flask
codecov.io for Angular:
Code coverage done right. Highly integrated with GitHub, Bitbucket and GitLab.
SKF codecov details:
https://codecov.io/gh/blabla1337/skf-flask
Requires.io pip packages:
Stay Up-to-date! Stay secure! Requires.io monitors your Python projects dependencies, and notify you whenever any of your dependency is out-of-date.
SKF Requires details:
https://requires.io/github/blabla1337/skf-flask/requirements/
uptimerobot.com:
Monitor HTTP(s), Ping, Port and check Keywords. Get alerted via e-mail, SMS, Twitter, web-hooks or push. View uptime, downtime and response times.
ssllabs.com & sslbadge.org:
ssllabs.org:
Bringing you the best SSL/TLS and PKI testing tools and documentation.
sslbadge.org:
Creates a nice badge for your website SSL/TLS security settings based on the Qualys SSL Labs testing.
License
Copyright (C) 2021 Glenn ten Cate, Riccardo ten Cate
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU Affero General Public License as
published by the Free Software Foundation, either version 3 of the
License, or (at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU Affero General Public License for more details.
You should have received a copy of the GNU Affero General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.
OWASP:
-
Owasp
Licensed under the creative commons license
Contributors
- Imanuel Febie
- Glenn ten Cate
- Riccardo ten Cate
- Lucas Luitjes
- Mattijs van Ommeren
- Alexander Kaasjager
- John Haley
- Daniel Paulus
- Erik de Kuijper
- Roderick Schaefer
- Jim Manico
- Martijn Gijsberti Hodenpijl
- Bithin Alangot
- Martin Knobloch
- Adam Fisher
- Tom Wirschell
- Joerg Stephan
- Simon Brakhane
- Gerco Grandia
- Ross Nanopoulos
- Bob van den Heuvel
- Mariano Jose Abdala
- Ilguiz Latypov
- Laurence Keijmel
- Rick Mitchell (Kingthorin)
- Xenofon Vassilakopoulos
- Heeraj Nair
- Alpha Kitonga
- Wojciech Reguła
- Amadeusz Starzykiewicz
- Adam Zima
- Kacper Madej
- Rafał Fronczyk
- Chang Xu (Neo)
- Martin Marsicano
- Priyanka Jain
- Chandrasekar Karthickrajan
- Leena Bhegade
- Balazs Hambalko
- Rudy Truyens
- Giulio Comi
- Aniket Surwade
- Thiago Luiz Dimbarre
- Harshant Sharma
- Semen Rozhkov
- Mehtab Zafar
- Daniel Spilsbury
- Akash M
- Tess Sluijter
- Xavier Rene-Corail
- Jacob O'Toole (on behalf of MeVitae)
- Luca Famà